
# Change Internet Access for Azure VMs 🖥️
Over the last few years, I had to do a lot of Azure Architecture Reviews of already existing customer environments or Azure Landing Zones. Thank God! 👍 Thus, I was able to help a lot of customers, making their Azure infrastructures way more secure and compliant! 🔐😊
Most architectures I reviewed grew over time ⌛and the aspects of enterprise scale and needed safe hybrid-connections 🔗had not been considered during the cloud journey. Therefore, almost every Azure Virtual Maschine (VM) was accessible from the public internet (inbound) and had unlimited access to URLs on the internet (outbound) 🌍. Unlimited internet access on an Azure VM can pose several risks and challenges, primarily related to security, cost, and performance as the following bullet point list explains:
– Security Risks
– Malware & Phishing
– Data Exfiltration & Data Leakage
– Bandwidth Costs
– Performance Issues & Network Congestion
– Compliance & Regulatory Concerns
– Compliance Violations
So far, if a VM has been spin up on Azure, even without an explicit public IP, the ‘default outbound access IP‘ is used for outbound connection to the internet. 😈 That means, by default the outbound internet access of a VM is not limited and all URLs should be accessible from this machine! 🙄
But now, Microsoft plans to retire default outbound internet connectivity for Azure VMs! 🥳🍾(Link)
In conclusion, a significant change is on the horizon for Azure VM networking, set to take effect on September 30, 2025. Microsoft is shifting towards a ‘secure-by-default‘ model, which will retire default outbound internet access for new Azure VMs. 🧱 Unlike the current setup, where Azure VMs can automatically access the internet, post-2025, new VMs will no longer have this feature enabled by default. This transformation is part of Azure’s broader initiative to enhance security. 🔐
However, there are options available to maintain outbound internet connectivity for VMs on Azure. You can choose explicit outbound methods, which grant you greater control, predictability, and traceability over the Azure VM’s internet access. Already existing VMs, as of the cutoff date, will remain unaffected, but any new VMs will need explicit configuration for outbound access! 👍🖥️
There are various approaches to configuring outbound connectivity:
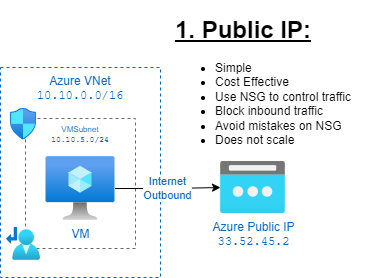
1. Public IP Address: 😒
The simplest and cost-effective method is to assign an Azure Public IP directly to the NIC of the Azure VM. You can connect a public IP to a VM, allowing it to route outbound traffic via that IP. But it is also the most unsecure option at the same time, as misconfiguration can lead to security issues quiet easily.
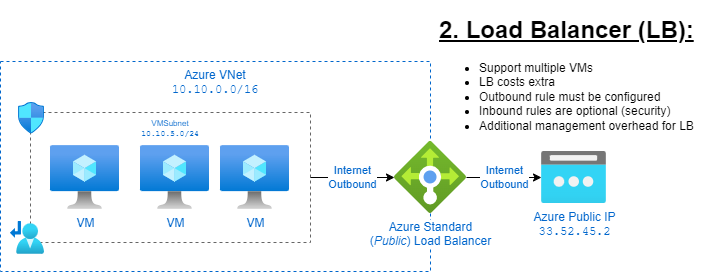
2. Standard Load Balancer with Outbound Rules: 😐
If you want to support multiple Azure VMs without individual public IPs, a standard (public) load balancer can be used. This involves attaching a public IP to the load balancer and creating outbound rules for the VMs.
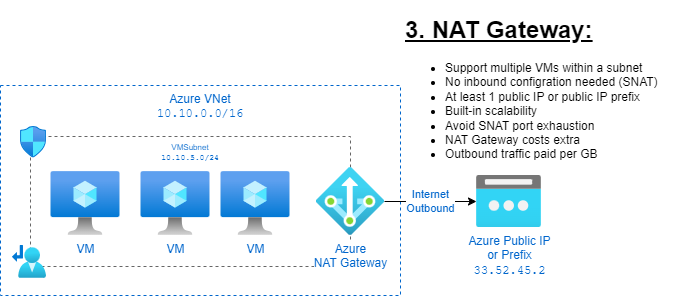
3. NAT Gateway: 😏
Providing outbound connectivity to all VMs within an Azure subnet, a NAT Gateway is an option. VMs configured to use this option will send outbound traffic through it, using its public IP for their outbound connections.
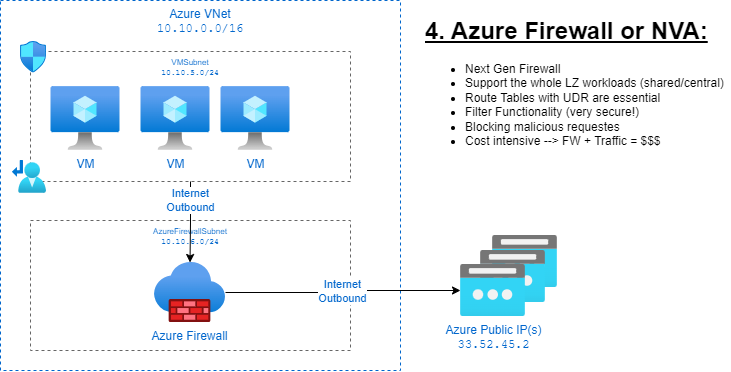
4. Azure Firewall or Azure NVA: 😊👍
If you require advanced security features, Azure Firewall can be used to manage outbound connectivity and filter traffic. It is a more expensive solution but provides robust protection, making it suitable for production environments. 🧱
As a summary, it is crucial to plan for this transition in advance to ensure the Azure VMs have the necessary outbound connectivity after the default access will be retired in September 2025. 📈 Microsoft is actively providing updates. Moreover, I going to help customers as a consultant through this transition as well, making it a manageable process for all my Azure customers. 👍
#AzureRocks 🤘#AzureVM 🖥️ #Community 💪
